
Click here to go see the bonus panel!
Hovertext:
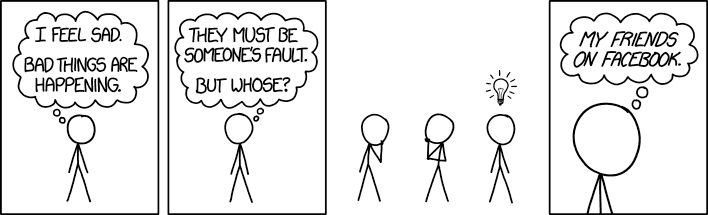
I love you, but I cannot accept your lifestyle.
Today's News:

Click here to go see the bonus panel!
Hovertext:
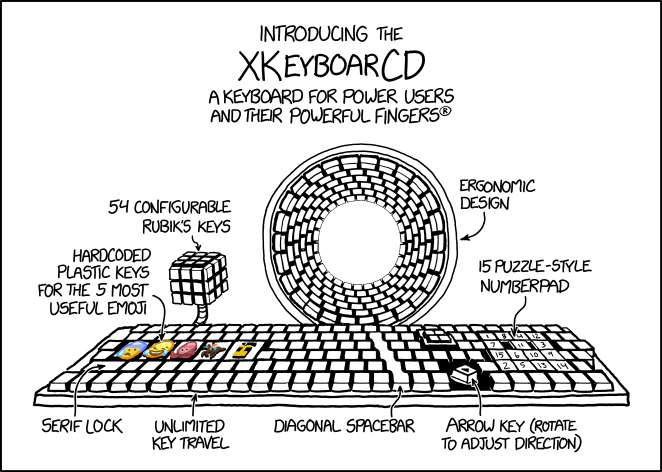
'Ha ha, Zuckerberg is a robot.' ***spends 14 hours motionless in front of a screen***
Today's News:
Next Page of Stories